Memority joins the S3NS Trusted Cloud Early Adopter Program
Memority has announced its entry into the Early Adopter Program (EAP) of S3NS's Trusted Cloud.


In light of Cybersecurity Awareness Month 2024 and the European Cybersecurity Month, I want to emphasize the importance of identity and access management (IAM) solutions in securing our digital environment.
As the Chief Information Security Officer at Memority, I am convinced that adopting these solutions is crucial for safeguarding both our company’s sensitive data and that of our clients. Below are four best IAM practices I encourage all organizations to adopt in order to enhance their security.
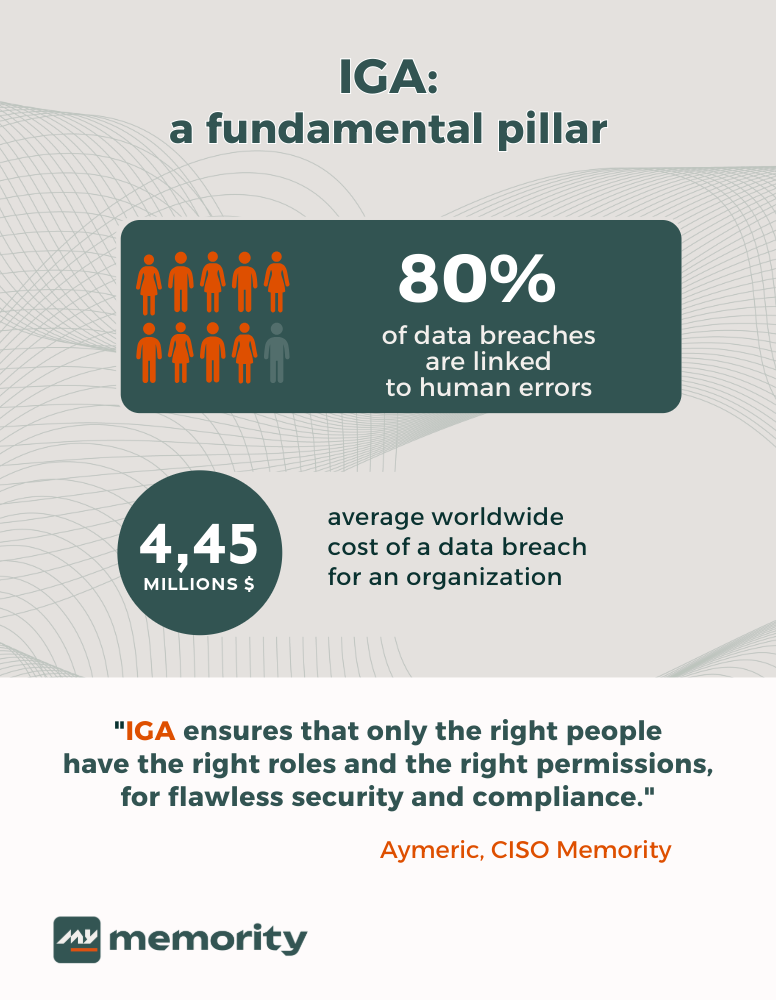
Identity Governance and Administration (IGA) is the cornerstone of a successful IAM strategy. It is vital for establishing rigorous access control within an organization. By implementing clear rules and role assignment processes, I ensure that each user – whether an employee, partner, or connected device – has the appropriate access rights. At Memority, our IT, platform, and HR systems are integral to this management, providing a comprehensive view of access permissions.
This enhanced visibility allows organizations to justify who has access to what resources and why. It also reduces internal risks by limiting access rights based on the principle of least privilege, ensuring that employees and partners have only the permissions necessary to perform their duties. This reduces the impact of accidental or malicious compromises. It’s also important to highlight the significance of audits and access reviews, processes that can now be automated, which were previously resource-intensive.
Additionally, IGA plays a key role in regulatory compliance. It addresses privacy law requirements, such as GDPR, but also extends to other regulations like NIS2 and DORA, as well as standards such as ISO 27001, ISO 27701, and SecNumCloud, which we have implemented at Memority. These ensure complete traceability of access and user actions.
In an environment where multiple applications and systems are the norm, Single Sign-On (SSO) and identity federation are essential solutions for simplifying access while enhancing security.
SSO allows users to authenticate once to access a suite of applications. This significantly reduces the risks associated with password management. Fewer passwords to remember translates to a lower risk of insecure behaviors (such as using simple or reused passwords or being inattentive during prompts). In addition to simplifying the user experience, this approach reduces the number of passwords reset requests, freeing IT teams from repetitive tasks.
The implementation of Single Sign-On (SSO) in all organizations is highly recommended. This approach simplifies users’ lives by enabling them to access all their applications with a single set of credentials. It alleviates the stress associated with managing multiple passwords and reduces the associated security risks.
I cannot overstate the importance of Multi-Factor Authentication (MFA) for securing critical access points. This method adds an additional layer of security by requiring multiple forms of identification, which has become essential in today’s cyber threat landscape.
Implementing MFA is one of the most effective measures for protecting user accounts. By combining multiple authentication factors (such as a password and a verification through a mobile device), MFA significantly complicates hacking attempts.
By integrating risk-based authentication (RBA) solutions, I ensure that the risk of each access is assessed in real time and that the appropriate authentication method is applied.
The combination of MFA and adaptive authentication strengthens system protection while ensuring flexibility to adapt to specific situations. On the Memority platform, these solutions apply to employees, partners, clients, and even connected devices.
Adopting an Identity as a Service (IDaaS) approach is a strategic choice that I strongly recommend. This approach centralizes IAM management in the cloud, providing secure access to resources from anywhere, which is particularly advantageous for a company like ours that supports remote work and operational flexibility.
The main advantage of the IDaaS model is its scalability. It easily adapts to the growth or changes within the organization without requiring additional internal infrastructure. It also enables organizations to leverage the previously mentioned benefits without the need for new deployments. Companies can focus on their core activities while benefiting from cutting-edge, modular identity management.
Furthermore, the IDaaS model seamlessly integrates SSO, MFA, and identity federation solutions, ensuring unified access management even at scale.
Finally, with Memority’s IDaaS, we benefit from a unified platform to manage all users, whether employees, partners, or clients. Through a self-service portal, users can independently manage their access and track their authentications, reducing the burden on IT teams.
Often overlooked or managed with complexity, IAM is the cornerstone of enterprise security in the digital age. By implementing robust IDaaS solutions that include IGA, SSO, identity federation, and multi-factor and adaptive authentication, organizations enhance their security while simplifying identity and access management. These best practices apply to all profiles: employees, partners, clients, and citizens, while ensuring an optimized user experience and protecting information systems against current threats.
Considering Cybersecurity Month, it is imperative to emphasize that identity management is a major issue impacting all levels of the organization. Whether you are a CEO, CISO, CIO, IT team member, or any other user, these IAM practices contribute to strengthened cybersecurity and improved risk management.