Memority joins the “French Tech 2030” promotion
Memority joins the 2025 “French Tech 2030” cohort, recognizing its commitment to France’s technological sovereignty.


In its My-Access offering, Memority provides a set of mechanisms for organizing and personalizing user authentication to federated applications, depending on their identity, the device and network they are using, and the application they wish to access. With Memority, we always adapt!
Let’s imagine a company, which we’ll call myCompany. In myCompany, we have, of course, internal employees, but also service providers. The myCompany employees have access to the hardware provided by the company – PCs and smart cards, for example – enabling them to access IS applications. Service providers, on the other hand, come to myCompany using their own equipment (supplied by their service company). They must still be able to access myCompany’s IS applications in order to carry out their work properly.
To make authentication as seamless as possible for in-house employees, Memority can offer a variety of authentication methods, such as Kerberos, Windows Hello or smart card authentication, and, in addition, set up context-dependent adaptive authentication rules. For example, Kerberos authentication can be triggered automatically and directly if the user is not on a cell phone. If this is valid, authentication is totally transparent to the user. If, on the other hand, Kerberos authentication fails (because the user is not on the myCompany network and/or not on a PC supplied by myCompany), then the other authentication modes available depending on the context can be proposed, such as the smart card, if this is detected on the workstation, or Windows Hello, if the user has previously enrolled the Windows Hello on the myCompany workstation. But what happens if an employee needs to access certain applications from a cell phone? As the previous authentication methods are limited to the PC, it is possible to add another method, such as login/password, which would then be available only to employees, and only on a mobile device. myCompany employees would then have 4 different means of authentication to access IS applications. What a choice!
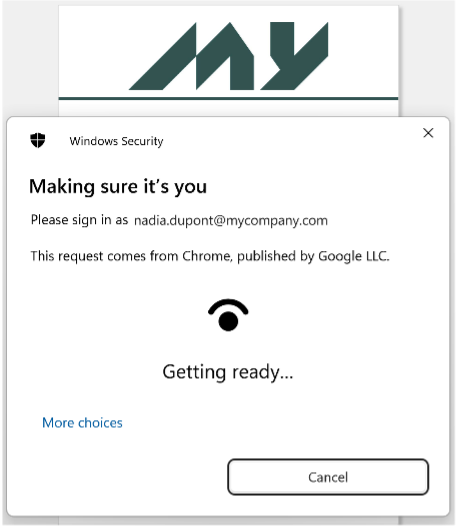
Automatic activation of Windows Hello on a PC

Automatic login/password authentication on mobile
But what about service providers? Since they don’t have any hardware supplied by myCompany, they can’t use Kerberos, Windows Hello or a smart card. Why not offer them the two-factor authentication capabilities of Memority’s My-Keys offer? On a PC, the service provider could enroll a browser. Memority authentication would then be possible only on this browser, and specifically on this workstation. Alternatively, the provider could use the Memority mobile app available on the Android and iOS app stores to receive push notifications to validate during authentication. If the service provider does not have a mobile provided by his own company and does not wish to install an application on his personal mobile, sending an OTP by SMS or e-mail can also be proposed. The My-Keys offer enables the management of these various second factors: it determines who can benefit from it, what the associated activation process is, what actions are available in self-service, and so on. And so, of course, only those authentication methods activated for/by the user will be offered to him/her at authentication. This means that service providers also have 4 authentication methods for accessing myCompany IS applications. Equality, no jealousy!
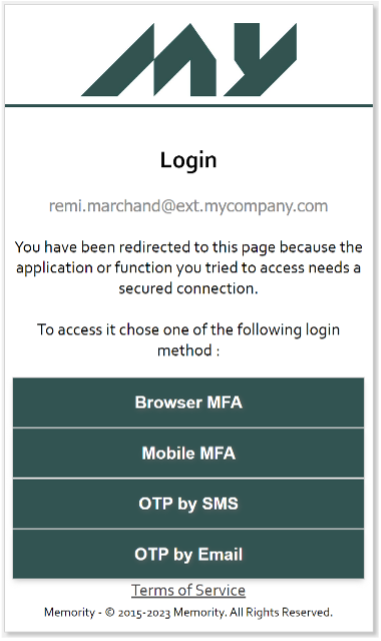
Authentication methods for service providers
In addition to all these criteria based on identity, device and network, there’s also the application accessed. For each authentication method defined at myCompany, a sensitivity level is defined. The same applies to each application federated with Memority. So, when accessing an application, whether you’re an employee or a service provider, on a PC or a cell phone, inside or outside the company network, only those authentication methods whose sensitivity level is equal to or higher than that of the application are possible and therefore proposed during authentication (in combination with the criteria defined above).
This is just an example, of course. The customization of Memority adaptive authentication can be simplified or, on the contrary, extended to include other available authentication means, other identity criteria, etc. With Memority, anything is possible!