Memority joins the S3NS Trusted Cloud Early Adopter Program
Memority has announced its entry into the Early Adopter Program (EAP) of S3NS's Trusted Cloud.


In 2021, a company managing the largest fuel pipeline in the United States suffered an attack that resulted in a severe gasoline shortage. The attack targeted an inactive account with a weak means of authentication not used by the company, which had neither deactivated nor deleted it. This type of account is known as an orphan account.
This example from the fuel giant shows that a single orphan account can have serious economic and reputational consequences!
There are many situations that can lead to the appearance of orphan accounts in a company’s information system. We’ll be covering them in the various episodes of this serie of articles dedicated to orphan accounts.
Orphan accounts are not/no longer attached to a physical user. This may be a user who leaves a company or moves up the hierarchy, but whose rights have not been deactivated or removed. It can also be an account created locally in an application, whether privileged or generic, but not attached to an identity.
Orphan accounts, and more generally poor identity lifecycle management, represent an increased risk of unauthorized access to sensitive data…
Identifying orphan accounts is therefore essential in IAM. Detecting them and proactively deactivating/deleting them helps protect against malicious access to a company’s IS.
Memority manages the entire identity lifecycle: from onboarding (when a user joins the company) and assigning the right roles and rights, to offboarding (when a user leaves the company) and deactivating and deleting all access rights.
The diagram below shows the lifecycle in the “Memority” approach. The identity is first created to enable support teams to prepare its equipment and potential accesses. At the start of his employment contract, the identity is activated, and his life in the company begins. Over time, the account can be updated, suspended or deactivated. Once the end of the contract has passed, the identity is deleted, access is cut off and authentication is no longer possible.
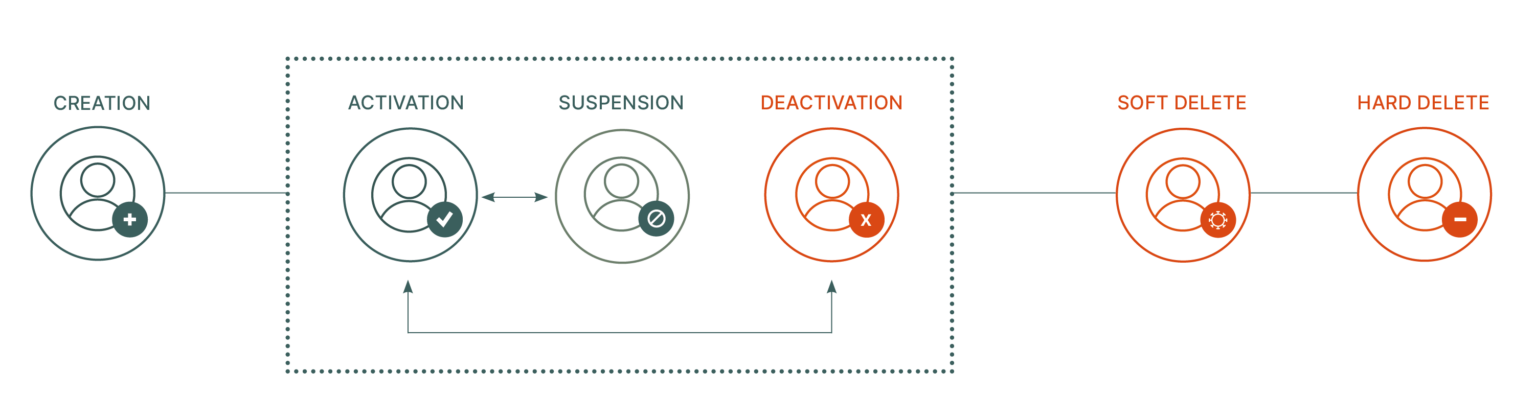
Controls are performed at account creation to prevent duplication of identities. Transfers from one entity/BU to another are also managed to control which rights/accesses should be assigned to the identity and which should be withdrawn. Finally, deactivation can be programmed, with a start date set at creation, or carried out manually, with immediate suspension of identity access.
Memority enables information to be cross-referenced with HR sources, indicating active employees and their arrival and departure dates, and IT sources, the active directory, integrating users, their accounts and their accesses. End-to-end lifecycle management ensures that a user’s departure does not result in the survival of compromising access. Once the identity has left, its accesses are automatically deactivated and then deleted following a grace period defined upstream.
Whether it’s a privileged account or a simple user, the policy remains the same for all, and particular attention is paid to their deletion on departure. It’s essential to assign the right rights to the right users at the right time, to guarantee the security of your information systems!
-> To find out more about the benefits of the Memority platform: click here